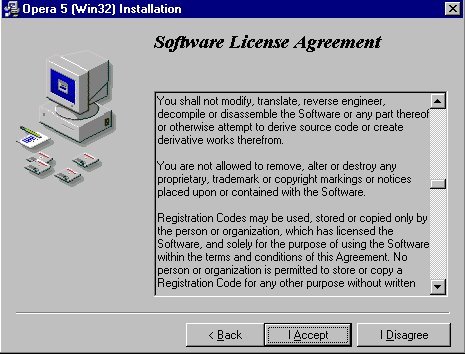
| |
You shall not modify, translate, reverse engineer,
decompile or disassemble the Software or any part thereof or otherwise attempt
to derive source code or create derivative works therefrom.
This is terrible. I NEED to decompile AND disassemble ANY software
entering my memory! Why should I trust it?
You are not allowed to remove, alter or destroy any proprietary, trademark or
copyright markings or notices placed upon or contained with the Software.
I should accept this? Why?
Registration Codes...
This does not interest us: even if it would be easy to find them on the
web we are NOT going to use any registration code...
|
As you see, we have a problem. If we click onto the I accept button, we are supposed
not to modify, translate, reverse engineer,
decompile or disassemble... but that's exactly what we want to do with any software that
enters our systems and that we may decide to use: there are enough malwares around...
I know, I know, this is the windoze world, it is not GNU/Linux... but what can we
do? Easy! If clicking on 'I accept' means we cannot reverse engineer,
then conversely clicking on
'No thanks' must mean that we CAN reverse engineer!
We just need a
'No thanks' button!
This is simple... at the
moment we have NOT yet clicked nutting, have we? So we may reverse engineer THIS SCREEN as much as we fancy...
a simple customizer
intervention will do the job:
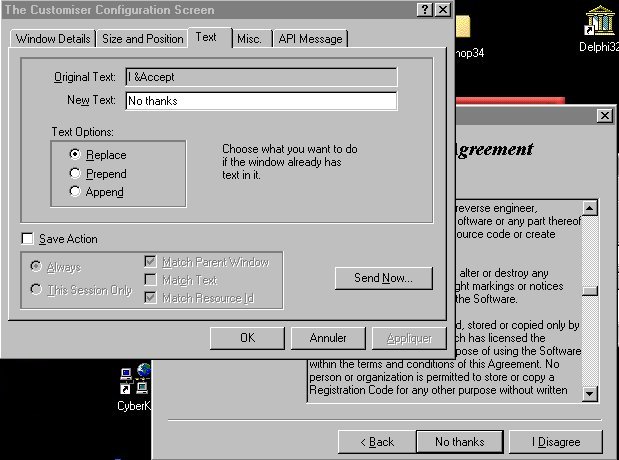
That's it, we may now proceed without breaking our EULA (end user licence agreement).
Our copy of Opera may now be 'tweaked' for study
purposes.
Descending inside Opera 5.0
As you can see on the big screen behind my shoulders, the advertisement window in
Opera 5.0 (this software will be our 'target' today) is located in the top right corner of the
main window.
In order to kill it we must identify the ad hoc drawing routine inside the code of our target. There are MANY
paths that you can follow, we'll take the 'dimensional' one today.
We'll start from the DIMENSIONS of the advertisement window, they must, of course, reside
as parameters
inside the target's code.
In order to calculate them most reversers would
use softice command hwnd -x when Opera is running.
Of course among Opera's many big and small windows
that softice will list, our specific advertisement window will be some sort of
multiple document interface (MDI) child window... since Opera is a
web browser that uses MDI, so that you don't have to open multiple
browsers to view a number of websites at the same time (an important
'secret' of Opera revealed :-)
In this specific case, as we'll
see in a second, our advertisement window will be a MDICHILD class window.
But forget this silly crackers' jargon and reversing approach: you don't even NEED to
know the reversing abc in order to fetch the data you need to kill it:
there's a MUCH MORE SIMPLER way to get at
the dimensions of this window. In fact, using a utility like our trusted customizer, you'll be able to fetch the
exact dimensional (and "nominal") data of this indecent (and soon to be eliminated)
window of ours.
Thus we fire the customizer again... see the yellow ball rolling on the big screen
behind
my shoulders?
Here we choose the 'edit window' option.
And then, in "windows details", with 'select' checked, we just
click onto 'on'...
this approach is so easy that even your aunt, or a microsoft certified software developer
could follow it.
Now move the customizer's 'big' cursor slowly towards our target.
AH! See how many 'hidden' windows are revealed while we are on our way there?
In fact there are a lot of "hidden processes" going on during any
'normal' windoze's session (and you can bet that someone, somewhere is taking
advantage of this matter of fact in order to gather data about you... but that's
another story). Let's simply ignore these hidden windows for now, you'll be able to play
with the customizer all by yourself at some other time... we
want to tackle our target now...
Identifying the culprit advertisement window
So, here we come to our advertisement window, here are the data as reported by the
customizer... "size and position": x position=328,
y position=4, height=64 and width=472... and, see, it is indeed a
BLD_MDICHILD window... an MDI child window as we supposed.
A small digression about the 'standardized' dimensions
of advertisement windows: as it happens
advertisement windows have often semi-standard heights and widths: in my experience
most advertisement windows
are rectangularly shaped in the range 62-64 (height) per 460-478 (width). Why this
"7 something to one"
relation (460/62=7.41 466/63=7.39; 472/64=7.37; 478/65=7.35)
should be (grossomodo) constant beats me, but nonetheless what counts is that
you can be reasonably sure that
somewhere inside the code of your average 'advertisement carrier' similar values will
be pushed onto the stack shortly before any window-drawing 'call' that will paint
the advertisement payload you're
supposed to HAVE TO WATCH all the time.
Let's start with the value we got: as we have seen this Opera's ad-window has following
dimensions (which are often enough standard in adwares):
The fixed 'start' advertisement image is just a somewhat smaller (468/60) OperaBanner.png image that you will
find inside your Opera/images subdirectory where you will be able to modify it
as much as you fancy, for instance:

Or whatever else you may
fancy :-) Note also that the people at Opera use
the png format. This deserves to be used waay more often on the web (instead of the 'proprietary' gif :-P
Anyway we would rather eliminate than simply change somehow an advertisement banner, n'est ce pas? The two decimal numbers that define the DIMENSIONS OF THE CONTAINING WINDOW 64 & 472 translate into 0x40 and Ox1D8 in
hexadecimal.
Since these two parameters must be pushed somewhere inside
the code, we
proceed
to disassemble our target (use either wdasm or [IDA])
and then we examine the 'dead listing' of the disassembled
code.
What are we looking for? Just the values 40 and 1d8?
No: we can be waaay more precise (if necessary we will afterwards always
'fall back' to 'broader' searches).
In fact we "should" find somewhere
inside
the code of our target BOTH our 40 & 1d8 dimensions values pushed on the stack.
It's cosmic power! Assembly is assembly: no matter
which 'higher' language has been used to program Opera, no matter which compiler has been
used to compile its code, a 'long' push is 68xxxxxxxx (with
inverted notation for the xxxxxxxx address)
whilst a 'short' push is 6Axx, therefore we'll of course look
for:
68D8010000 = push 000001D8 (note the inverted notation D801!)
and
6A40 = push 00000040
I won't annoy you now with the possible slack variants or register variants of these values.
Besides there's no point in being excessively cracking-smart here, since these
values are in effect
pushed "as such" inside Opera: note that since BOTH these parameters are to be pushed
in order
to set the
width and height of
a given window, they
will mostly be situated very near to each other inside the code.
Thus let's simply
fetch the code snippet where "our" width and height values are pushed inside the code.
Jumping here from 6D35(Conditional)...
6D3A A1A8305900 mov eax, dword ptr [005930A8]
6D3F 3BC6 cmp eax, esi
6D41 743D je 406D80
6D43 6A54 push 54
6D45 6A40 push 40 ;height
6D47 68D8010000 push 1D8 ;change to 6800000000 (push 0) and kill ads
6D4C 81C128FEFFFF add ecx, FFFFFE28
6D52 57 push edi
6D53 51 push ecx
6D54 56 push esi
6D55 FF7014 push [eax+14]
Note that this snippet holds the ONLY TWO references to both
68D8010000 = push 000001D8
and
6A40 = push 00000040
that do exist in the whole 'dead listing' of our target... :-)
That's called a BINGO! in crackers' jargon :-)
We're not finished, eh.
As you can see from the snippet above, the routine is conditionally
called from 6D35.
Let's have a look
6D18 FF15C8A55500 Call dword ptr [0055A5C8] ;GetClientRect
6D1E 3975DC cmp dword ptr [ebp-24], esi
6D21 7448 je 6D6B ;of course an unconditional jump would avoid
;the call below and eb48 (jmp 6D6B no matter
;what) would kill our targeted ads as well :-)
6D23 8B4DAC mov ecx, dword ptr [ebp-54]
6D26 8BD9 mov ebx, ecx
6D28 2B5DA4 sub ebx, dword ptr [ebp-5C]
6D2B 81EBDB010000 sub ebx, 1DB
6D31 6683FB64 cmp bx, 64
6D35 7D03 jge 6D3A ; call "vulgar_advertisement_settings"
6D37 6A64 push 64
6D39 5B pop ebx
Note that THERE ARE MANY OTHER POSSIBLE APPROACHES TO KILL AN ADVERTISEMENT... or, more globally,
to find your mustard inside overbloated code... for instance
you could proceed also using the nice "colour" approach (window's
background is pale yellow? Let's say F3F55B?
Well by now you should know what you should be looking for in the dead listing :-)
Note that a 'positional' as opposed to 'dimensional' approach is also possible...
This concludes today's conference. We went a long way, from the macrocosmos of the
structure of
the web to the microcosmos of Opera inner workings and assembly code. And yet these
two dimensions are more correlated than one would think, and -what is more
disturbing- the more you'll try to study and understand them, the more you'll realize that
there is even more to understand, lest you be taken
advantage of unknowingly.
Understanding searching and reversing matters is
of paramount importance in a world of hidden codes, secret meanings and concerted propaganda,
where you are supposed NOT EVEN TO UNDERSTAND what's going on.
Never before the old words: Fac sapias, et liber eris have been
so true and I'm convinced that the clever students of the most brilliant and famous
university in France should and will understand this.
I am honored of having being invited here. Any questions?
fravia+
#include "standard_disclaimer.h"
««««« Back to paris5.htm ««««« »»»»»
Back to paris.htm »»»»»
(c) III Millennium by [fravia+],
all rights reserved and reversed



